Why Fabric?
12 July 2024
#FCAteam

Imagine a network that’s easy to manage, extremely secure, and ready to scale instantly. Such possibilities are offered by an innovative solution based on Fabric technology, consisting of three key elements: Fabric Connect, Fabric Attach and Fabric Extend. Thanks to these technologies, you can create virtual networks that are not only easy to configure, but also resilient and flexible.
- Fabric Connect – is based on the SPB 802.1aq and IS-IS protocols, which ensure reliable packet transport in the network core and effective management. Thanks to this technology, we can create virtual networks for each service that are easy to configure, secure and easily scalable. Moreover, reconfiguration of such networks is quick and usually requires only modifications at the edge of the network, which minimizes the risk of errors and simplifies management.
- Fabric Attach – extends Fabric Connect to endpoint devices that don’t support this technology, allowing you to map endpoint access to selected services that are configured on edge switches, ensuring consistency throughout network and ease of management.
- Fabric Extend – allows you to connect Fabric Connect via WAN, e.g. the Internet, so you can connect many geographically scattered locations into one Fabric Connect network. Fabric Extend can be implemented, for example, using an SD-WAN gateway, which provides flexibility and scalability in creating large-scale networks.
Fabric is an ideal solution for companies and organizations that need a reliable, flexible and efficient network infrastructure, ready for changing needs. Thanks to this technology, network management becomes simpler, faster and more resilient.

Easy to manage
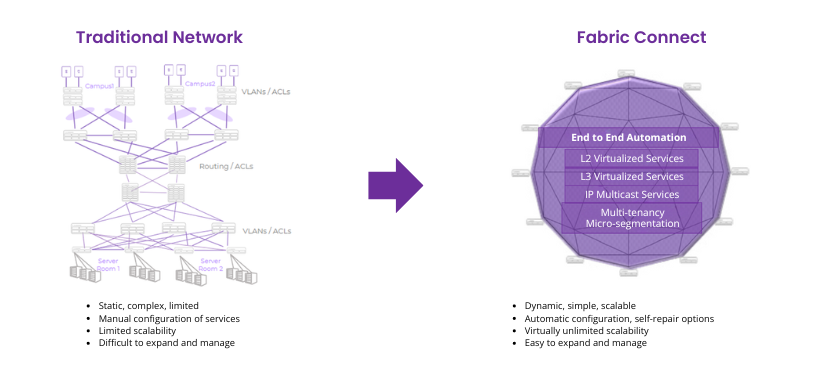
In traditional networks, management requires the configuration of many protocols, such as VLAN, STP, OSPF, or PIM, which can be time-consuming and complicated. Each protocol must be configured separately on each device on the network, which increases the risk of errors and increases the time needed to make changes.
With Fabric Connect, management becomes simple and effective. In the network core, configuration only needs to be done once during deployment, using just a few commands. When configuring new services, for example, it is enough to define a VLAN and assign it an I-SID on edge switches. Typically, these are only two commands for each access switch, which significantly simplifies the process and minimizes the risk of errors.
Greater resistance to configuration errors
Traditional networks require configuring services based on a complex protocol stack, which means that misconfiguration of one protocol can result in the failure of many services or even the entire network. In the case of Fabric Connect, thanks to the SPB protocol, the services are independent of each other, which means that an error in the configuration of one service usually does not affect the operation of the others.
In traditional networks, changes often need to be made outside of business hours to avoid disruptions, requiring additional planning and preparation for possible problems. Thanks to the independence of services in Fabric Connect, the risk of disruption is so low that changes can usually be made during business hours without fear of downtime. Updates are carried out quickly and unnoticeably, which significantly reduces the time of network unavailability.
Fault tolerance
In a Fabric Connect network, if a link fails or a switch goes down, traffic is almost immediately switched to an alternative route. The switches have previously prepared routes, it eliminates the need to recalculate them, as is the case in traditional networks. Thanks to this, the switching is so fast that it is difficult to lose even one ping.
Automatic onboarding of new switches
New switches equipped with Fabric Engine are automatically configured when connected to other switches with the same system. They recognize their neighborhood and integrate with the rest of the infrastructure without the need for manual configuration.
Redundancy that doesn’t require sacrificing resources
In a Fabric network, you don’t have to worry about loops, and the more connections between switches in the core, the better. All links are active and therefore no available bandwidth is wasted, unlike using loop prevention protocols that block ports.
Scalability
Fabric technology uses MAC-in-MAC encapsulation, which allows it to support thousands of users at the edge of the network, while maintaining a minimum number of MAC addresses in the core – corresponding to the number of switches. In addition, Fabric allows the creation of over 16 million I-SIDs, which is a huge advantage compared to the number of traditional VLANs, ensuring almost unlimited scalability.
Security
MAC-in-MAC encapsulation primarily improves security by ensuring traffic anonymity for external observers. Only devices at the edge of the network are aware of the MAC address of the end device. There are no IP addresses in the core, so there is no way to suspect encrypted traffic in other network segments.
Extreme Networks is funding prizes for a Hackathon for participants who would be able to find a way to move between network segments running on Fabric Connect – but so far no one has succeeded. This is a proof of how safe and reliable this solution is.
Easy and resource-saving multicast management
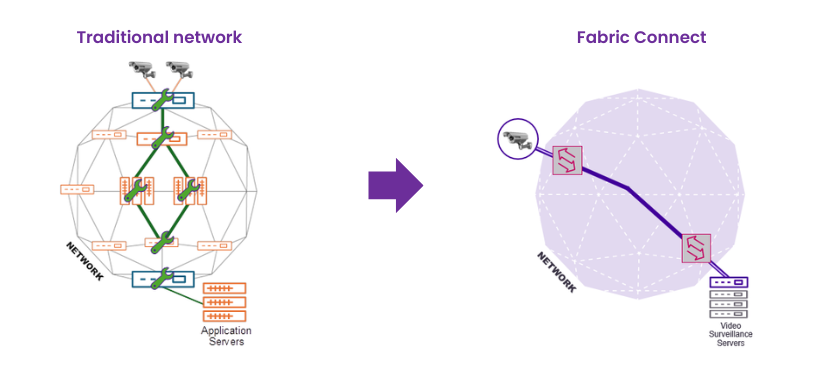
Fabric natively supports multicasts, without additional use of the PIM protocol, which is very useful, e.g. in environments with a large number of cameras. Multicast traffic is replicated only where necessary and only when a peer requests to listen, minimizing unnecessary network load.
APs extend Fabric to the wireless network
Thanks to access points from Extreme Networks, Fabric Attach can be used by users connected wirelessly. Each user receives the appropriate I-SID, ensuring consistency and security for both wired and wireless connections.
ExtremeControl combined with Fabric means even greater security
Integration of Fabric Connect with NAC ExtremeControl, using a database such as Active Directory, enables precise allocation of access to network resources based on groups or individual users. Services are available only when the user is connected and authenticated, regardless of his location – in Krakow, Warsaw, or the method of connection to the network, wireless or wired. I-SIDs and VLANs are created after authentication, and immediately after disconnection they disappear and the ports switch to unauthenticated mode.
ExtremeControl and Fabric makes configuration even more automated
When using ExtremeControl and Fabric Connect, you don’t even need to configure services on edge switches – you only configure policies in the central management system. Switches receive information from ExtremeControl about what tunnels should be created for each user.

Are you interested in this solution?
Contact us!
